Phishing? What’s that all about then? Lots of vague nautical references and some veiled threats about losing something.
Well in fact, phishing and variants are one of the fastest growing forms of online fraud and the impacts have been enormous.
‘Gone’ = losses resulting from whaling emails (Crelan Bank, $76m losses in Jan ’16 | Ubiquiti, $47m in Aug ’15)
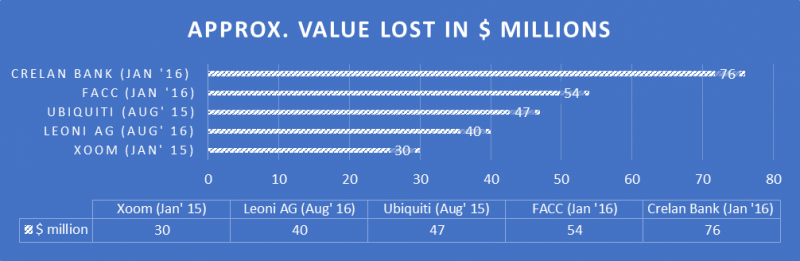
Fig. 1 – Five of the largest financial losses to organisations as a result of whaling emails – National Cyber Security Centre, ‘Phishing – what is it and how does it affect me?’ – link
But don’t think when I say ‘online fraud’ these attacks are always highly sophisticated assaults engineered by skilled and well-funded hacking outfits. They’re not.
These types of fraud are just another example of social engineering, the aim of which is to encourage their victims to do something that on the surface seems innocent enough, but through bypassing normal approval channels often leads to serious impacts.
Impact so serious in fact that Jeh Johnson, Homeland Security Chief, cites spear phishing as one of the top threats to organisations where “the most devastating attacks…begin with the simple act of spear-phishing” – link
“CEO sacked after aircraft company grounded by whaling attack” – FACC, €50m losses in Jan ’16 – link)
While carrying out these attacks can require very limited amounts of technical knowledge, they do require a certain amount of staging and coordination and are mercifully easy to stop if you know what to look for. Attacks typically:
- Originate from an email
- Contain personalised information about the targeted organisation or individual
- Convey a sense of urgency
- Are crafted with a solid understanding of business language and tone
That said, the levels of sophistication being used to craft these targeted attacks are increasing, with research from cybersecurity product vendors such as ProofPoint indicating that cyber-criminals are starting to use large databases of personal information and automated tools to personalise these emails on a mass scale.
Where whaling emails used to be not much harder to identify than their less targeted phishing counterparts, recent adoption of fluent business terminology, industry knowledge, personal references and spoofed email addresses have made sophisticated whaling emails difficult for even a cautious eye to identify.
Highly targeted content is now combined with several other methods which executives should be aware of to reduce their chances of falling victim to a whaling attack. Crucially all these developments either exploit existing trusted relationships, or combine a cyber-attack with non-cyber fraud tactics.
So what can you do to protect yourself and your organisation? Well there are a number of common sense steps, as well as some more specific activities, that can improve your chances of avoiding such an attack.1
Training
Knowledge is power, and awareness of these threats inside your organisation can drastically reduce the chances of someone falling foul to an attack
“It’s especially critical that finance, payroll, and human resources departments be alert for these scams as nearly 50 percent target the CFO and 25 percent target HR inboxes. Impostor messages often ask employees to keep things confidential and bypass normal approval channels. Employees should be suspicious if they receive a request for unusual information or a wire transfer via email. Check the reply-to email address and always call to confirm the request.”
Technology
Given that all forms of phishing attack start with email, not receiving that email in the first place is the most obvious way of preventing it.
“The protocol for sending email in common use today is the Simple Mail Transfer Protocol (SMTP), originally adopted 1982. SMTP email was not designed with security in mind because the few people who had email accounts tended to be military personnel and academics who had security clearances. SMTP email is inherently unsecure in transit and in storage.” – Absio Corporation, Demystifying Secure Email
As part of a sensible risk management strategy, it’s important you choose and use tools that represent a proportionate response to the level of sensitivity or risk presented by succumbing to an attack of this kind.
Consider using a secured email provider to prevent unsolicited emails from reaching their targets in the first place, whilst ensuring your sensitive and private communications remain that way.
There are several strong offerings available from software vendors that understand the importance of balancing strong and secure, end-to-end email encryption with end-user ease of use.
Whilst not apparent at first, ease of use for a product is a top security concern. As security that is difficult to use tends to be avoided.
Luck
Sadly luck plays a part in avoiding these and similar attacks as according to the National Cyber Security Centre (https://www.ncsc.gov.uk), organisations have to accept that a “successful whaling attack is a possibility” given the increase in sophistication in recent times
“It is crucial to remember that whaling is a means of social engineering, and malicious actors will use methods exploiting established trust structures, existing outside the cyber realm, to reassure the victim. Simply making your employees aware of social engineering threats doesn’t make them invulnerable; some attacks are too well crafted and no amount of user awareness and training can guarantee their detection. Employee and executive training on social engineering tactics should be considered part of a series of technical and user based defences against attacks, but recognise the limitations of such measures.”
“Similarly, whilst organisations should ensure training is supported by hardened technical defences, malicious actors are increasingly employing techniques to evade automated detection and prevent analysis of attack methodology. As such, organisations should accept that a successful whaling attack is a possibility, and put in place checks and processes to mitigate the damage.” – National Cyber Security Centre, ‘Phishing, Whaling: how it works, and what your organisation can do about it?’ – link
The summary
The takeaway from all this? Start the awareness today – not just personally, but organisationally.
And don’t think just because the size of the organisations or scale of their losses currently grabbing the headlines doesn’t align to the size or your business. Mitigating risk is about weighing up the impact of a loss on your business. How much would it take to bring your business to a close?
Mix awareness and training with the right tools, processes, checks and balances. Like fire doors, each of these layers can stop the damage from spreading and could just save your business.
Don’t leave the fate of your business to chance
About the Author
Simon Wright is the CEO of Britecloud (LinkedIn) a UK software distributor specialising in cloud-based security and productivity solutions that drive value and return-on-investment for organisations of all sizes.
Britecloud recommends ‘Dispatch’ secured email solutions from Absio to reduce the impact of cybercrime on your organisation. For more details visit https://absio.britecloud.com or call +44 (0) 203 876 5221 to discuss how quickly you could start protecting you and your business today.

